Web Design Blog
I've seen many sites recommend using 1280x720 resolution but I'll do you one better: 1920x1080 (full HD). Logic being, you can always shrink it later and not lose quality.
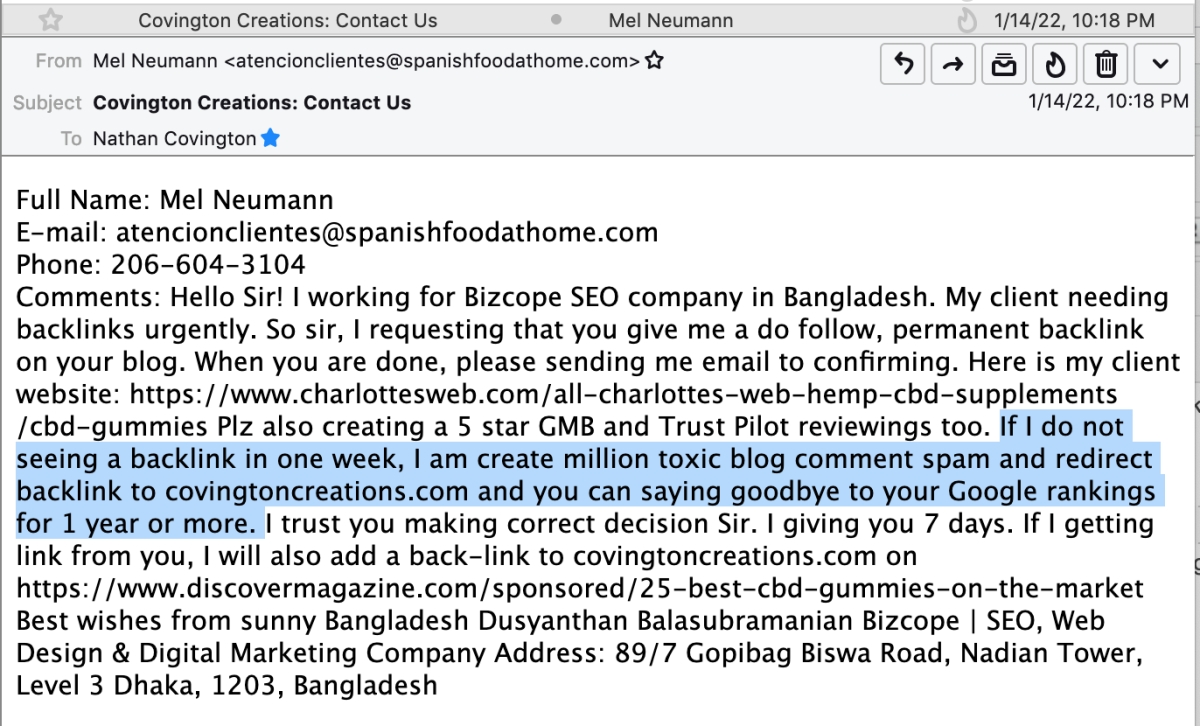
I frequently receive emails from various SEO partners that ask me to add links on my articles to their client's site, a pretty normal "link building" technique. This one caught me off guard because this is the type of thing that requires finesse, not threats.
Nevertheless, this guy asked for a link back to his CBD client, a 5 star GMB review, a 5 star Trust Piliot review...
Users of the web hosting service GoDaddy had their accounts compromised for months before learning about the breach. The attackers were also able to compromise websites’ security certificates.
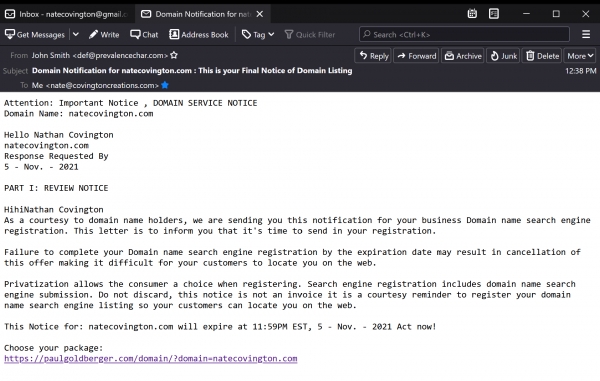
SCAM ALERT! Coming from PaulGoldberger.com domain:
Below is a copy of the (horribly written) message that I received -
This Notice for: yourcompany.com will expire at 11:59PM EST, 5 - Nov. - 2021 Act now! Choose your package: https://paulgoldberger.com/domain/?domain=yourcompany.com
Attention: Important Notice , DOMAIN SERVICE NOTICE
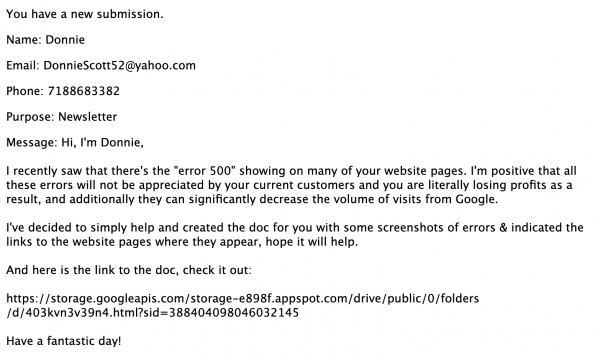
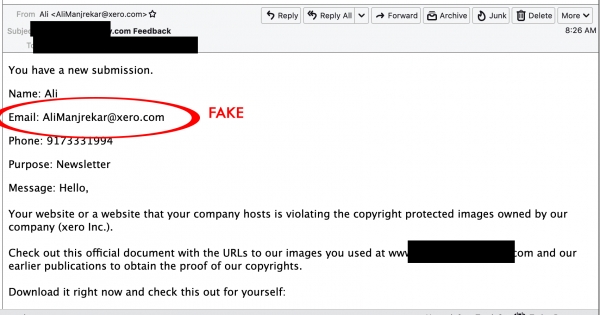
Beware of these types of messages that are coming through website's contact forms:
Email: This email address is being protected from spambots. You need JavaScript enabled to view it.
Phone: 7188683382
Purpose: Newsletter
Message: Hi, I'm Donnie,
I recently saw that there's the "error 500" showing on many of your website pages. I'm positive that all these errors will not be appreciated by your current customers and you are literally losing profits as a result, and additionally they can significantly decrease the volume of visits from Google.
Your website or a website that your company hosts is violating the copyright protected images owned by our company
I've been getting these spammy messages through my contact forms lately, figured I would share so that others don't get rattled by this type of nonsense.
I made the following video to walk through and discuss the traditional "hamburger" menu as it compares to the Off-Canvas sidebar.
The short version is the off-canvas sidebar option gives a lot more power: it can be used for more than just the mobile menu.
Watch the video to discover the ins and outs!
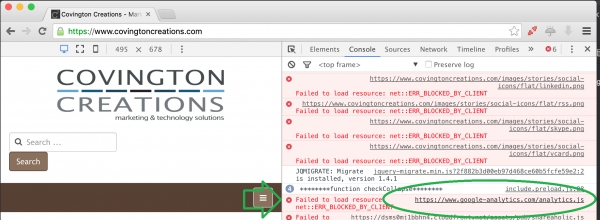
Lately I've been wondering if the Google Analytics script is going extinct. A recent political campaign gave me some statistics to examine, and I'm having a tough time reconciling Google Analytics data with my web server stats. It seems the web server, and the CMS, are reporting a lot more traffic than Google recognizes, likely because Google Analytics' script is blocked by many ad block scripts, privacy oriented browsers, etc.
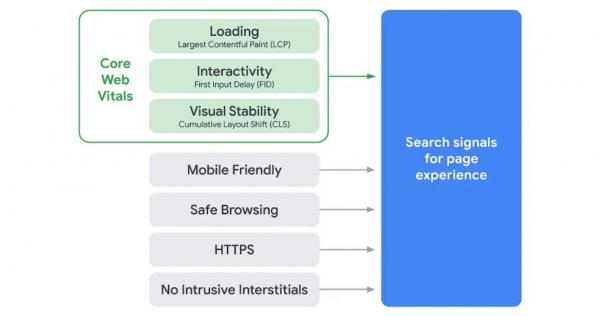
Google is announcing Core Web Vitals will become ranking signals in May 2021 in an update that will also combine existing UX-related signals.
The ‘page experience’ signal combines Core Web Vitals with the following signals:
- Mobile-friendliness
- Safe-browsing
- HTTPS-security
- Intrusive interstitial guidelines
Core Web Vitals were introduced earlier this and are designed to measure how users experience the speed, responsiveness, and visual stability of a page.
Free consultation?
Book now. No commitment.
hello@covingtoncreations.com
will reply in 24 hrs
570.508.6881 (or SMS)
9-5 mon-fri
Design & Development
Wordpress, Drupal, Joomla
New custom websites, bespoke themes and extensions, redesigns, upgrades, migrations
Optimization & SEO
Let us optimize and manage your overall online presence. We offer full service monthly SEO as well as one-time projects.
Maintenance, Patching
White glove monthly backups, security updates, maintenance and testing for your Wordpress, Drupal, or Joomla site.